Bypassing HTTPS
In the previous section, we saw how to sniff and capture any packets sent over HTTP requests. Most famous websites like Google, Facebook uses HTTPS instead of HTTP. This means when we try to become the MITM, when the person goes to that website, the website will display a warning message saying that the certificate of that website is invalid. That’s why the person won’t log in to that page. So, we are going to use a tool SSLstrip. This tool is used to downgrade any HTTPS request to HTTP. So whenever the target person tries to go to any website, they’ll be redirected to the HTTP page of this website.
Let’s go to the browser on the target, and we are going to try to go hotmail.com. Now, in the following screenshot, we can see that on the top in the address bar the website uses HTTPS, so if we try to become the MITM, this website will display a warning:
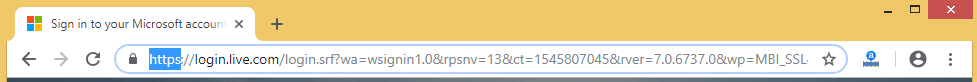
To bypass the warning, we are going to use a tool called SSLstrip to downgrade any request to the HTTPS website and get it redirected to the HTTP version of this website. Once we go to the HTTP version, sniffing the data will be trivial, exactly like what happened in the previous section.
MITMf starts SSLstrip automatically for us, but we can use it manually. We are actually going to run exactly the same command that we saw in the previous section as shown in the following screenshot:
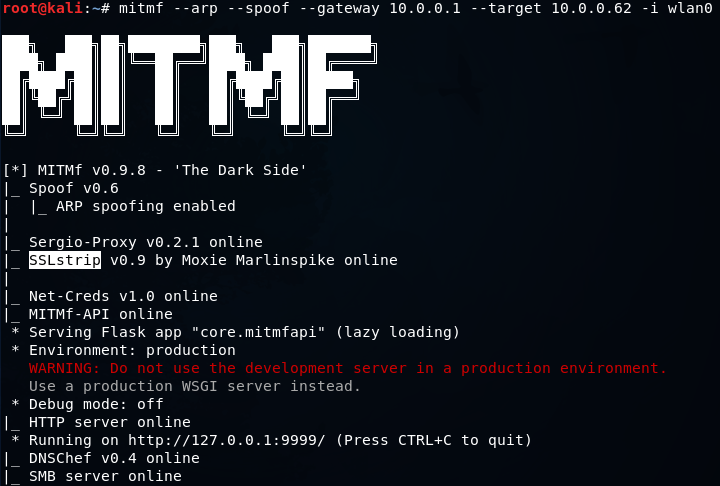
In the above screenshot, we can see that it will actually tell us that SSLstrip has been started and it’s online. Now, we’re going to go back on the Window device, and we’re going to go to hotmail.com. Now instead of the HTTPS version, we are actually going to go to the HTTP version of hotmail.com. We can see this in the following screenshot:
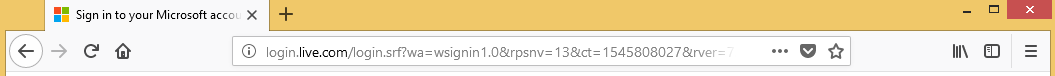
In the above screenshot, we can see that there is no HTTPS, so we are at the HTTP version of the website. We will also notice that we didn’t see any warning, so it just looks like exactly a normal website of hotmail.com.
So, we are going to put our email and password, and we are going to sign in. Now, we will go to our Kali machine, and see that we managed to capture the email as [email protected] and we also managed to capture the password as 123456:
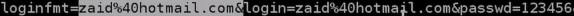
Websites such as Google, Facebook, Skype are actually using HSTS. In HSTS, the browser comes in with a pre-hardcoded list of websites that have to be browsed as HTTPS. So, even if we try to downgrade the HTTPS connection to HTTP, the browser will refuse to show the website, and just show an HTTPS version of it. This is because, without connecting to anything, the browser has a list stored locally on the local computer saying that it shouldn’t open Facebook, Gmail, and such websites as HTTP. So, whatever way we try to do it, the website will just refuse to open in HTTP.
