Metasploit commands
In this section, we will learn the basic command of Metasploit and the exploit’s use on a vulnerable machine as Metasploitable. Some basics commands of Metasploit are search, back, info, help, and exit.
Use of back and exit commands
In Metasploit, the use command activates a particular module, and on the basis of that module, it changes the msfconsole’s content.
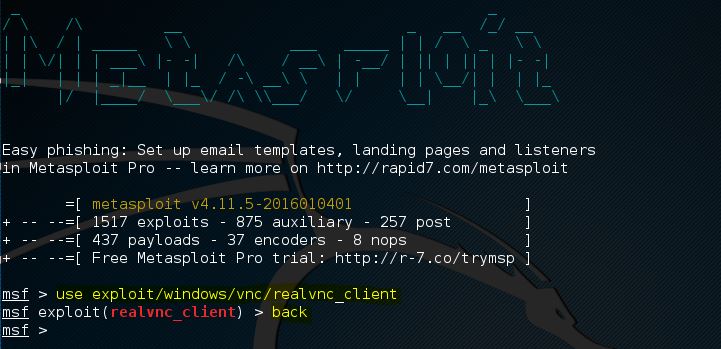
In the above screenshot, the command line’s content is changed to the exploit named realvnc_client. Now the information of this exploit can be retrieved, required parameters of the exploit can be set, and the parameter can run against the target.
The use of back command will be required if we wish to leave the content of the exploit and switch back to msfconsole. We will back to the msfconsole after using the back command. Now we can switch to another module of Metasploit by again using the use command. The msfconsole will be closed by using the exit command. After this command, we will back to the terminal of Kali Linux.
Help command
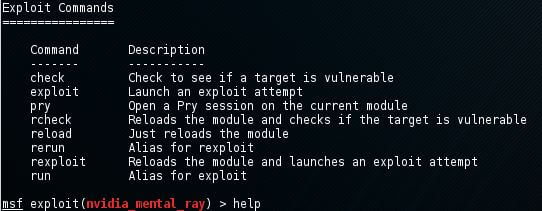
The list of all possible commands, including the description, is given by the help command. If we select any active exploit, we can get the list of exploit command by using the help command, which is shown as follows:
Info command
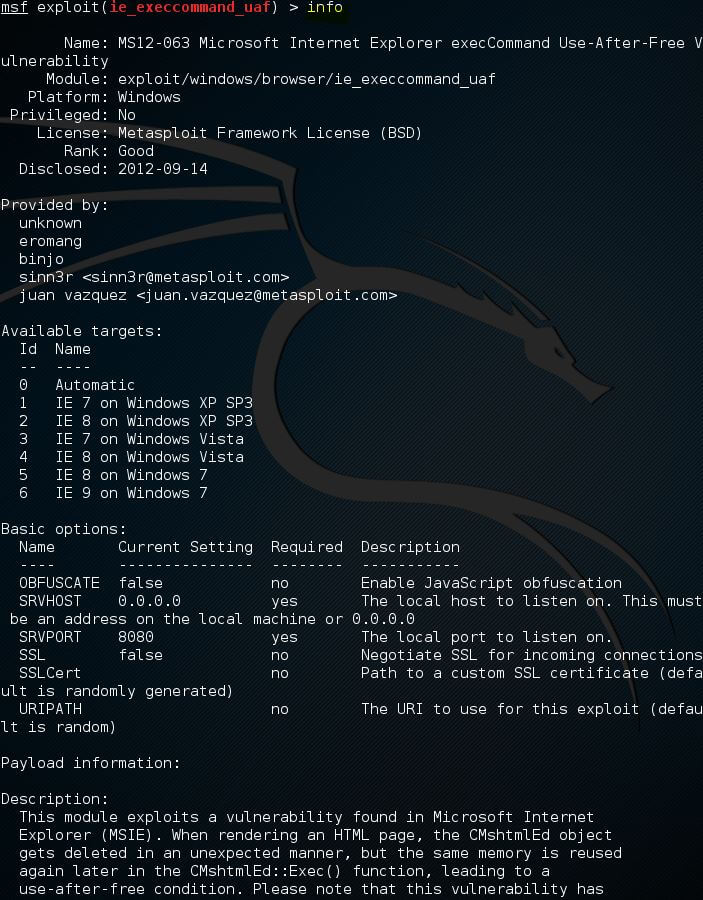
When we select an exploit using the use command, we can use the info command to get information like available target author, name, platform, and a lot more. Now we will do an exploit called ie_execcommand_uaf by using the info command:
Search Command
Metasploit contains a large number of different exploits, around 1.500, and new exploits are added regularly. So it becomes very important to know about the number of exploits using the search function. The search function will be used very easily by applying a search command, which is followed by the search term. For example, suppose we want to know the exploit related to Flash player, so we will use flash as the search term. In the following screenshot, we use the search command followed by a flash, as shown below:
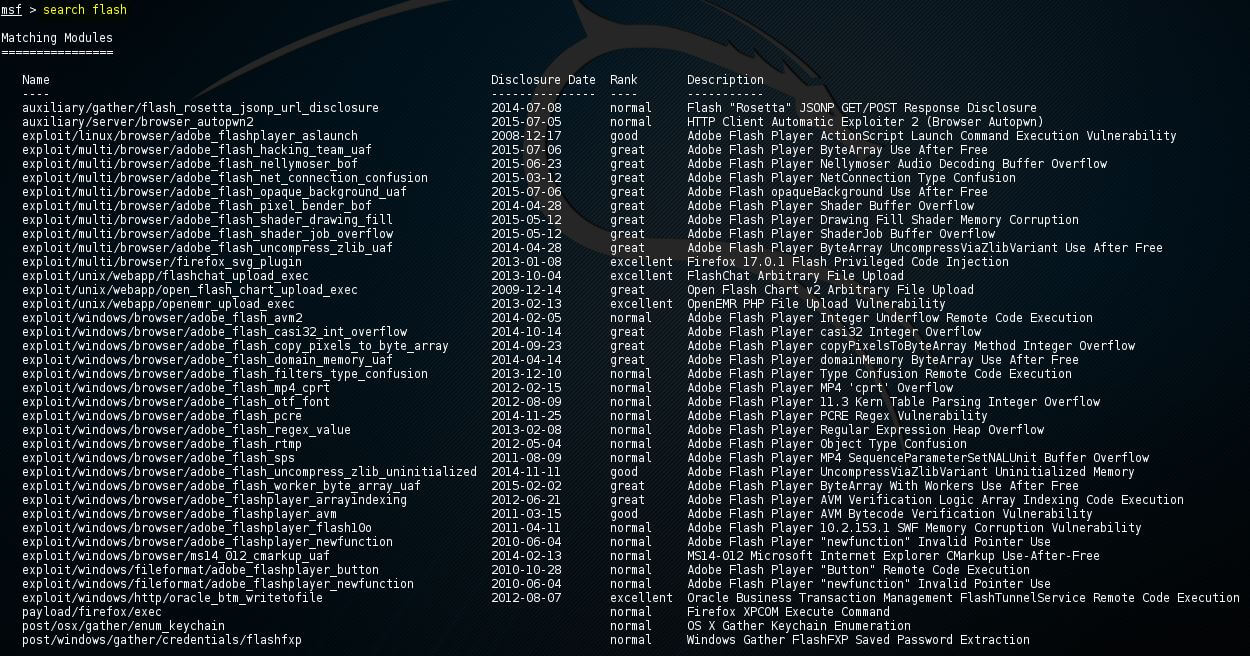
In the above screenshot, we can see that flash player software has a lot of exploits, and all the exploits are shown above.
Metasploit command for keywords
We have learned the use of Metasploit commands, which are used in the activation of an exploit on msfconsole. We have also learned the use command to change the context of the command line to the exploit. Now we will learn about the exploit parameter, how to show them by using the set command, and how to change them. How we can show the targets, evasion, advanced and payload option will also learn in this section. The available parameters for the command show will be displayed using the help show command, as shown below:

Show options
If the command line is in the context of an exploit, available parameters for an exploit will be shown by the show options command. Now we will use the exploit named adobe_flash_shader_drawing_fill with the use command as follows:
Followed by the command show options
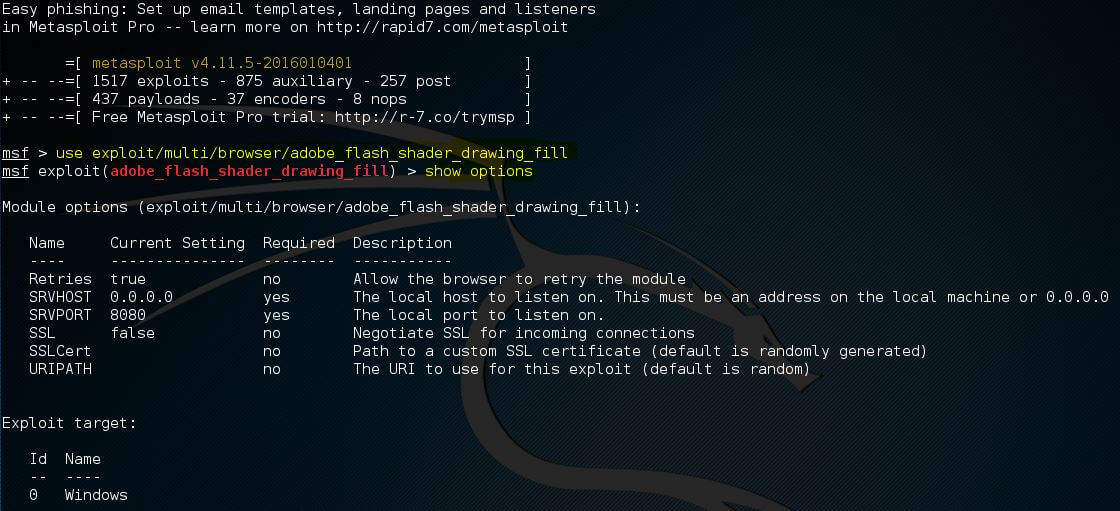
In the above screenshot, total 6 options are contained in the flash exploit, and we are required only 2:
- Retries
- SRVHOST (Required)
- SRVPORT (Required)
- SSL
- SSLCert
- URLPath
Under the module option, the currently selected target is returned by the show options command. For the selected exploit, 0 is the default target, which is Windows.
Now we will use the set command to change the default values. The option name and new value will follow the set command:
The value of SRVHOST will be changed to 192.168.0.100 by using the command Set SRVHOST 192.168.0.100. The port 8080 will be changed to 80 by using the command Set SRVPORT 80.
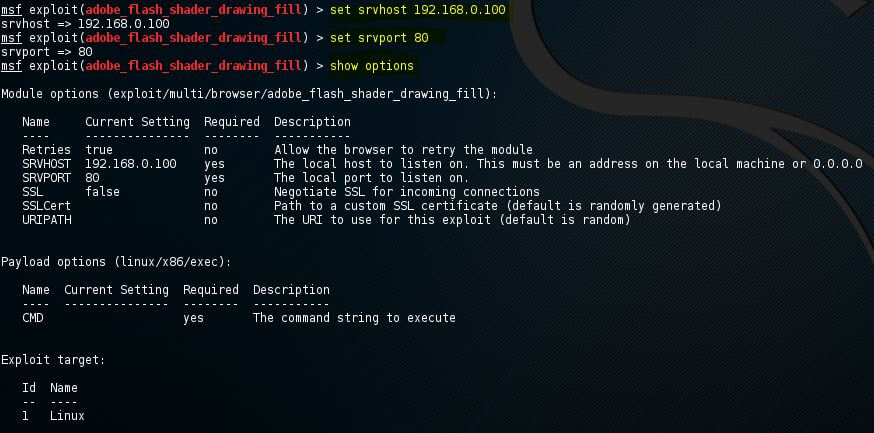
The changed value of SRVHOST and SRVPORT can be verified by again using the show options command. Using the set command, we can change the values of Boolean. The set command will be followed by option name and true or false.
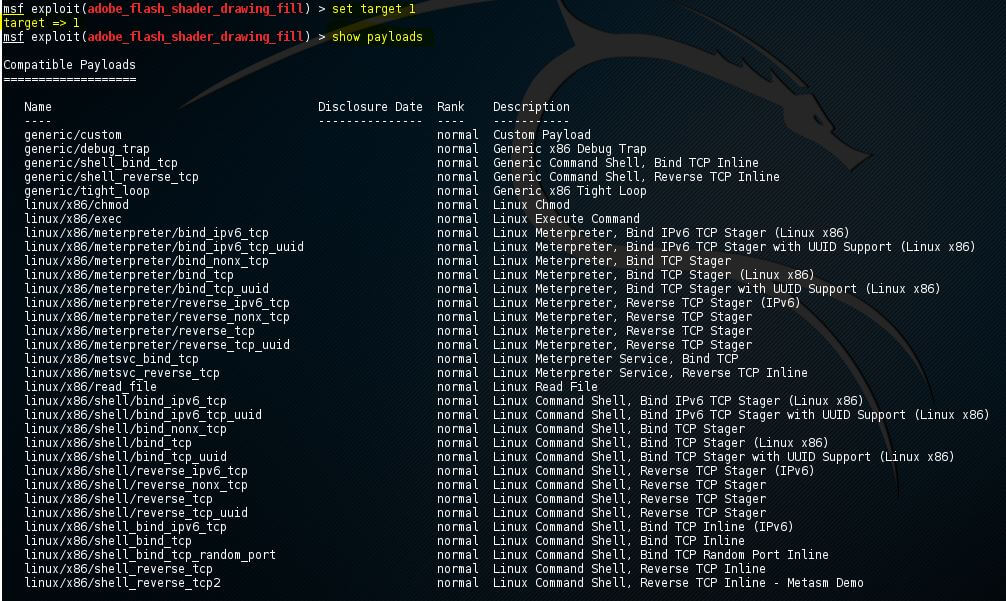
Show payloads
For the exploit, a list of compatible payloads will be returned by msfconsole using the show payloads option. In the given example of flash player exploits, a few compatible payloads are returned by msfconsole as follows:
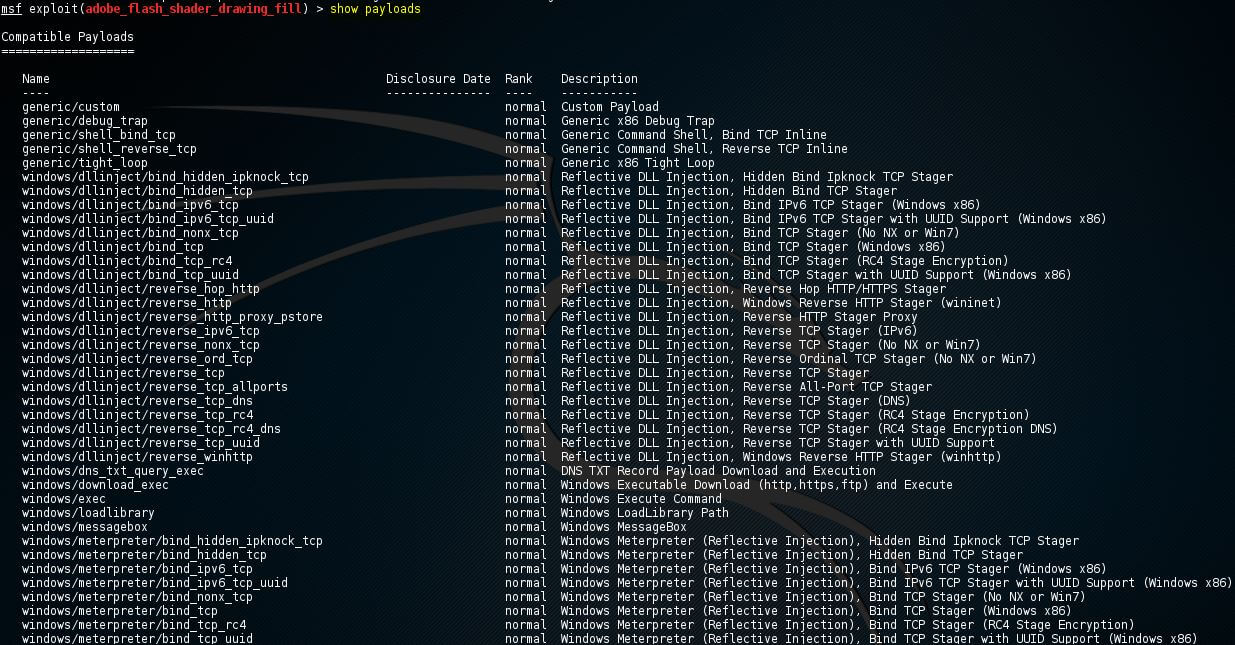
Now we will use the set command to use the certain payload with the payload name as follows:
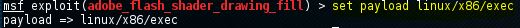
In the above screenshot, we have set the payload as linux/x86/exec.
Show targets
A list of OS which has vulnerability in the selected exploit is retuned by the show target command.
For the exploit named adobe_flash_shader_drawing_fil, the following output will be returned when we run the show targets command as follows:
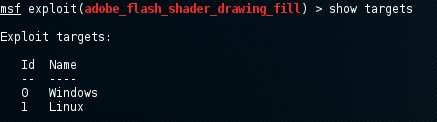
The Linux and Windows operating system is targeted by this exploit. If we want to know more information about exploits and targets, the info command can be used. Now we will use the set command to set a target with the target ID as follows:
The list of payloads can be reduced by setting the targets because it will show only those payloads with which the target seems compatible:
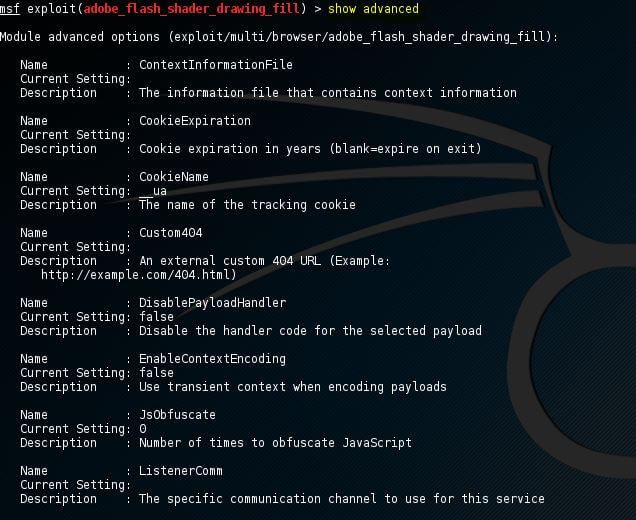
Show advanced
For the exploit, if we want to look at the advanced options, we can use show advanced command as follows:
If we want to change the advanced settings, we will use the set command with advanced parameters and the new value as follows:
Show encoders
The compatible encoder will be returned by the show encoders command. Simple IPS/IDS is evaded by the encoders, which are looking for certain bytes of our payload as follows:
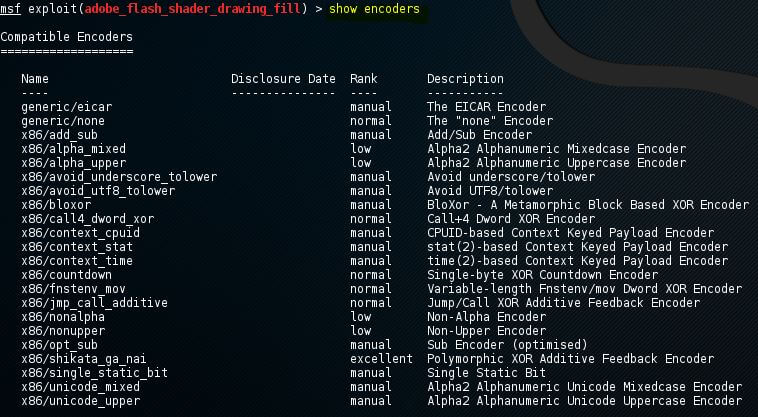
We will use the set command with the encoder name to use an encoder.
Show nops
The list of NOP generators will be returned by the show nops command. NOP stands for No Operation. If we want to bypass the simple IDS/IPS signature of common NOP sleds, NOP will be used to change the NOP sled’s pattern. Using the CPU architecture, the generators of NOP will start.
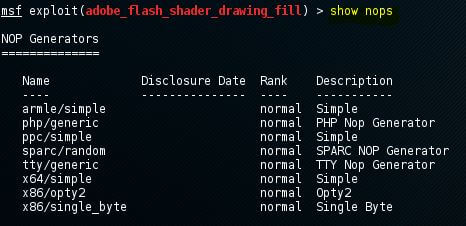
We have to use the set command with the NOP generator’s name if we want to use a NOP generator. The NOP generator will take the NOP shield when we launched the exploit.
Show evasion
If we want to show the list of evasion techniques, we can use the show evasion command.
We will use the set command with the parameters of evasion and the new value to change the setting of evasions.
Metasploit commands for exploit execution
Suppose we are doing an exploit, and we have set all the required options, including payloads and advance settings like encoding, evasion options and NOP generator. In that case, the exploit is set to be executed. Using the two commands like an exploit and run, we can execute the exploit. In the msfconsole, we have to type exploit or run and exploit will run.
