Nmap
Ordinary people have a common issue with the internet system because the internet is very complicated for them, and they are unable to understand them. Even if the person uses a system that is small home-based, it is also extremely complicated for him. The internet system’s complexity will grow exponentially if the persons are from agencies or larger companies that deal with many computers, around hundreds or even thousands of computers. On the internet, the problem of identifying activity can be solved by using the Nmap. It is used to scan the whole system and make a map of its every part.
Nmap is a type of program that tells us about the open port and those rules. The network is used by the computer for connection is scan by this program. As an output, it will provide the lists of ports, operating system, device name, and many other identifiers to help the user understand the connection status details.
Nmap stands for Network Mapper. It is an open-source tool that is used for security auditing and network exploration, and this tool is freely available. In 1997, Gordon Lyon, the security expert, wrote that under the GNU General Public License, the solution has remained openly available. GUI tool versions, Command line, and *nix, MAC, Windows operating system X version exist.
A tool is typically used by administrators and security professionals for network scanning using raw IP packets. Using this, users are allowed to discover various details about the composition of infrastructures like existing firewalls, versions or names of the application, operating systems, available hosts, and many more. Using the command line, the core utility can be executed. That’s why various implementation of GUI (Graphical user interface) are freely available.
While hacking on a system, if the hacker gets uncontrolled ports, they will provide Nmap to gain access to it. If we are a hacker and want to get successful access to the target system, we will use our target system to run Nmap, and then we will look for vulnerabilities and find out how to exploit them. The software platform is not only used by hackers. It is often used by IT security companies to find out the types of attacks that could be potentially faced by the system.
Working of Nmap
When the network is checked for the hosts and services, at that time, Nmap will work. Once found, the information related to those services and hosts is responded to by the software platform. The response is read and intercept by the Nmap. After that, Nmap uses the information of hosts and services and create a network map. The map that is created by Nmap contains detailed information on how the hosts are connected, who use the port, listening to any arriving security issue, what is doing by each port, and what is and is not making it by the firewall. All of these can be accomplished by the Nmap because it utilizes the script’s complex system that is used to communicate with the network’s every part. Communication between the human users and network components is possible because of scripts. Nmap uses those types of scripts that are capable of network discovery, backdoor detection, vulnerability detection, and vulnerability exploitation. Nmap can be described as a piece of software that is extremely powerful, but if we want to use it correctly, we need a good deal of background knowledge.
Nmap is mostly used by Internet security companies to scan their system and find out the existing weakness on the system that could be used by the hacker to potentially exploit. Using this, the companies can work on their system’s weaknesses. If we want to scan the network for weaknesses and open ports, we will use the program called Nmap. It is one of the more common tools to do this because it is open source and free. At Holm Security, very effective ways can be used to use this technology as we provide excellent security service on the web, making sure that the ports of our users remain securely closed to unauthorized persons.
To provide the safety of things like sensitive information, Nmap can provide pre-emptive and the level of knowledge whether we are a government agency that is protecting the highly sensitive data, a major corporation, or a private user that has sensitive information on their computer.
Metasploitable
Metasplotable is a kind of vulnerable VMware virtual machine which is released by the Metasploit team. The reason to release Metasploitable is that when we learn how to use the framework of exploitation, we will face one of the problems that are trying to determine and configure the targets so that we can do attack and scan.
A vulnerable Linux virtual machine is described by the Metasploitable, which can practice common techniques of penetration testing, test security tools, and conduct security training. We can use visualization technologies like Virtual box and any recent VMware products to run the VM (virtual machine). We can say that kali Linux is the opposite of Metasploitable. If we want to hack into other devices, we will use Kali Linux. We will use the Metasploitable if we want to hack into it. Metasploitable is specially designed for persons who are interested to learn penetration testing. The various vulnerabilities are contained by the Metasploitable. So, we are going to hack into Metasploitable using Kali Linux. Therefore, Metasploitable will become one of our machines, victim, or target.
We can use the following link to download the Metasploitable.
https://information.rapid7.com/metasploitable-download.html.
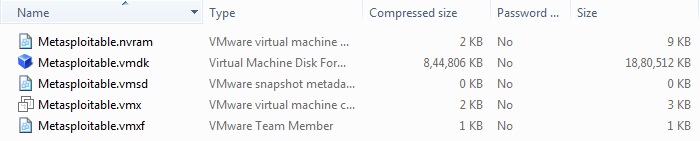
After downloading that file, we will get a zip file, which is shown as follows. When we decompress the zip file, we will get a directory named metasploitable-linux-2.0.0.zip. We will double click on this directory, and then we will get the following files:
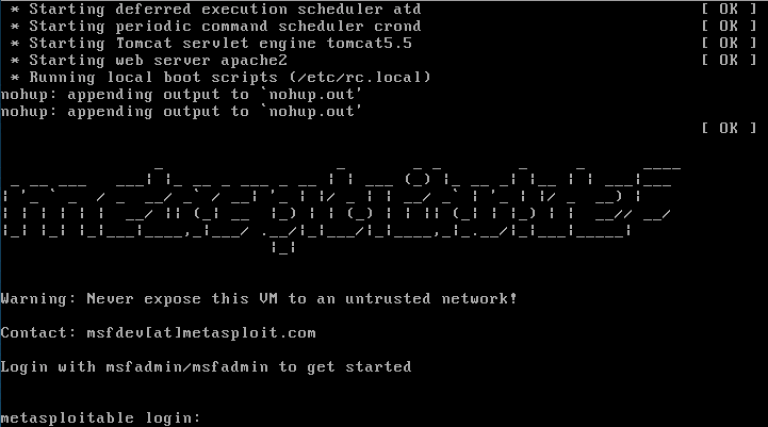
After spending a brief time, our system will be booted, and then it is ready for action. msfadmin:msfadmin is the default login id and password.
If we want to know more about the VM configuration, we can go to the Rapid7 website because it contains a Metasploitable 2 Exploitability Guide. But we should beware of it because it has some spoilers.
