PPP Protocol
The PPP stands for Point-to-Point protocol. It is the most commonly used protocol for point-to-point access. Suppose the user wants to access the internet from the home, the PPP protocol will be used.
It is a data link layer protocol that resides in the layer 2 of the OSI model. It is used to encapsulate the layer 3 protocols and all the information available in the payload in order to be transmitted across the serial links. The PPP protocol can be used on synchronous link like ISDN as well as asynchronous link like dial-up. It is mainly used for the communication between the two devices.
It can be used over many types of physical networks such as serial cable, phone line, trunk line, cellular telephone, fiber optic links such as SONET. As the data link layer protocol is used to identify from where the transmission starts and ends, so ISP (Internet Service Provider) use the PPP protocol to provide the dial-up access to the internet.
Services provided by PPP
- It defines the format of frames through which the transmission occurs.
- It defines the link establishment process. If user establishes a link with a server, then “how this link establishes” is done by the PPP protocol.
- It defines data exchange process, i.e., how data will be exchanged, the rate of the exchange.
- The main feature of the PPP protocol is the encapsulation. It defines how network layer data and information in the payload are encapsulated in the data link frame.
- It defines the authentication process between the two devices. The authentication between the two devices, handshaking and how the password will be exchanged between two devices are decided by the PPP protocol.
Services Not provided by the PPP protocol
- It does not support flow control mechanism.
- It has a very simple error control mechanism.
- As PPP provides point-to-point communication, so it lacks addressing mechanism to handle frames in multipoint configuration.
It is a byte-oriented protocol as it provides the frames as a collection of bytes or characters. It is a WAN (Wide Area Network) protocol as it runs over the internet link which means between two routers, internet is widely used.
PPP has two main uses which are given below:
- It is widely used in broadband communications having heavy loads and high speed. For example, an internet operates on heavy load and high speed.
- It is used to transmit the multiprotocol data between the two connected (point-to-point) computers. It is mainly used in point-to-point devices, for example, routers are point-to-point devices where PPP protocol is widely used as it is a WAN protocol not a simple LAN ethernet protocol.
Frame format of PPP protocol
The frame format of PPP protocol contains the following fields:
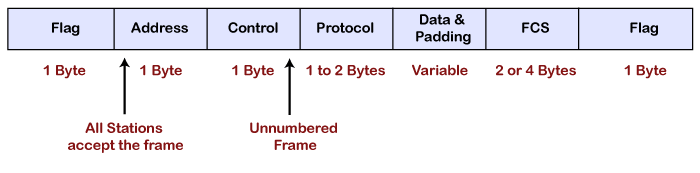
- Flag: The flag field is used to indicate the start and end of the frame. The flag field is a 1-byte field that appears at the beginning and the ending of the frame. The pattern of the flag is similar to the bit pattern in HDLC, i.e., 01111110.
- Address: It is a 1-byte field that contains the constant value which is 11111111. These 8 ones represent a broadcast message.
- Control: It is a 1-byte field which is set through the constant value, i.e., 11000000. It is not a required field as PPP does not support the flow control and a very limited error control mechanism. The control field is a mandatory field where protocol supports flow and error control mechanism.
- Protocol: It is a 1 or 2 bytes field that defines what is to be carried in the data field. The data can be a user data or other information.
- Payload: The payload field carries either user data or other information. The maximum length of the payload field is 1500 bytes.
- Checksum: It is a 16-bit field which is generally used for error detection.
Transition phases of PPP protocol
The following are the transition phases of a PPP protocol:
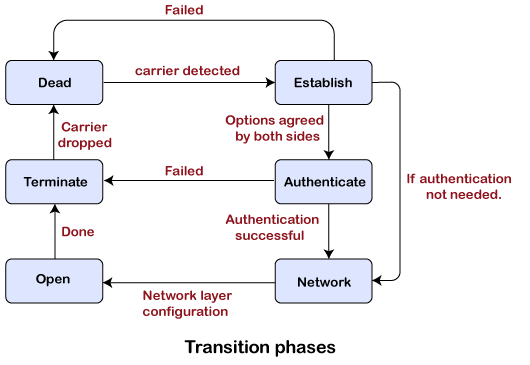
- Dead: Dead is a transition phase which means that the link is not used or there is no active carrier at the physical layer.
- Establish: If one of the nodes starts working then the phase goes to the establish phase. In short, we can say that when the node starts communication or carrier is detected then it moves from the dead to the establish phase.
- Authenticate: It is an optional phase which means that the communication can also moves to the authenticate phase. The phase moves from the establish to the authenticate phase only when both the communicating nodes agree to make the communication authenticated.
- Network: Once the authentication is successful, the network is established or phase is network. In this phase, the negotiation of network layer protocols take place.
- Open: After the establishment of the network phase, it moves to the open phase. Here open phase means that the exchange of data takes place. Or we can say that it reaches to the open phase after the configuration of the network layer.
- Terminate: When all the work is done then the connection gets terminated, and it moves to the terminate phase.
On reaching the terminate phase, the link moves to the dead phase which indicates that the carrier is dropped which was earlier created.
There are two more possibilities that can exist in the transition phase:
- The link moves from the authenticate to the terminate phase when the authentication is failed.
- The link can also move from the establish to the dead state when the carrier is failed.
PPP Stack
In PPP stack, there are three set of protocols:
- Link Control Protocol (LCP)
The role of LCP is to establish, maintain, configure, and terminate the links. It also provides negotiation mechanism.
- Authentication protocols
There are two types of authentication protocols, i.e., PAP (Password Authenticate protocols), and CHAP (Challenged Handshake Authentication Protocols).
1. PAP (Password Authentication Protocols)
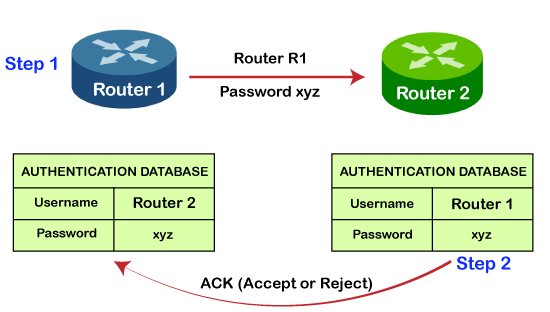
PAP is less secure as compared to CHAP as in case of PAP protocol, password is sent in the form of a clear text. It is a two-step process. Suppose there are two routers, i.e., router 1 and router 2. In the first step, the router 1 wants to authenticate so it sends the username and password for the authentication. In the second step, if the username and password are matched then the router 2 will authenticate the router 1 otherwise the authentication failed.
2. CHAP (Challenged Handshake Authentication Protocol)
CHAP is a three-step process. Let’s understand the three steps of CHAP.
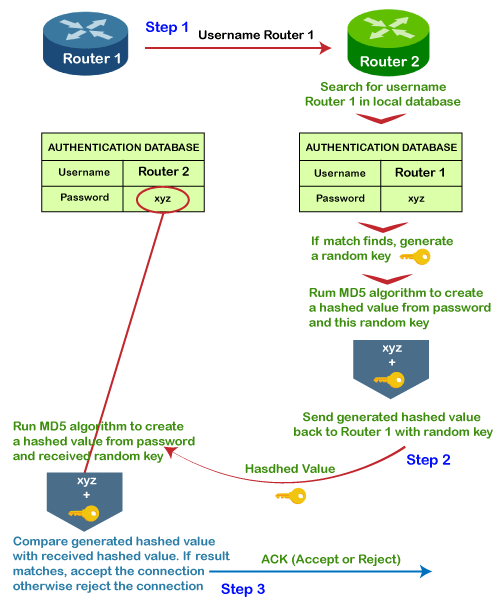
Step 1: Suppose there are two routers, i.e., router 1 and router 2. In this step, router 1 sends the username but not the password to the router 2.
Step 2: The router 2 maintains a database that contains a list of allowed hosts with their login credentials. If no data is found which means that the router 1 is not a valid host to connect with it and the connection gets terminated. If the match is found then the random key is passed. This random key along with the password is passed in the MD5 hashing function, and the hashing function generates the hashed value from the password and the random key (password + random key). The hashed value is also known as Challenge. The challenge along with the random key will be sent to the router 1.
Step 3: The router 1 receives the hashed value and a random key from the router 2. Then, the router 1 will pass the random key and locally stored password to the MD5 hashing function. The MD5 hashing function generates the hashed value from the combination of random key and password. If the generated hashed value does not match with the received hashed value then the connection gets terminated. If it is matched, then the connection is granted. Based on the above authentication result, the authentication signal that could be either accepted or rejected is sent to the router 2.
- Network Control Protocol (NCP)
After the establishment of the link and authentication, the next step is to connect to the network layer. So, PPP uses another protocol known as network control protocol (NCP). The NCP is a set of protocols that facilitates the encapsulation of data which is coming from the network layer to the PPP frames.
