Protection in Operating System
Protection is especially important in a multiuser environment when multiple users use computer resources such as CPU, memory, etc. It is the operating system’s responsibility to offer a mechanism that protects each process from other processes. In a multiuser environment, all assets that require protection are classified as objects, and those that wish to access these objects are referred to as subjects. The operating system grants different ‘access rights’ to different subjects.

In this article, you will learn the protection in the operating system with its needs, goals, and authentication.
What is Protection in Operating System?
A mechanism that controls the access of programs, processes, or users to the resources defined by a computer system is referred to as protection. You may utilize protection as a tool for multi-programming operating systems, allowing multiple users to safely share a common logical namespace, including a directory or files.
It needs the protection of computer resources like the software, memory, processor, etc. Users should take protective measures as a helper to multiprogramming OS so that multiple users may safely use a common logical namespace like a directory or data. Protection may be achieved by maintaining confidentiality, honesty and availability in the OS. It is critical to secure the device from unauthorized access, viruses, worms, and other malware.
Need of Protection in Operating System
Various needs of protection in the operating system are as follows:
- There may be security risks like unauthorized reading, writing, modification, or preventing the system from working effectively for authorized users.
- It helps to ensure data security, process security, and program security against unauthorized user access or program access.
- It is important to ensure no access rights’ breaches, no viruses, no unauthorized access to the existing data.
- Its purpose is to ensure that only the systems’ policies access programs, resources, and data.
Goals of Protection in Operating System
Various goals of protection in the operating system are as follows:
- The policies define how processes access the computer system’s resources, such as the CPU, memory, software, and even the operating system. It is the responsibility of both the operating system designer and the app programmer. Although, these policies are modified at any time.
- Protection is a technique for protecting data and processes from harmful or intentional infiltration. It contains protection policies either established by itself, set by management or imposed individually by programmers to ensure that their programs are protected to the greatest extent possible.
- It also provides a multiprogramming OS with the security that its users expect when sharing common space such as files or directories.
Role of Protection in Operating System
Its main role is to provide a mechanism for implementing policies that define the use of resources in a computer system. Some rules are set during the system’s design, while others are defined by system administrators to secure their files and programs.
Every program has distinct policies for using resources, and these policies may change over time. Therefore, system security is not the responsibility of the system’s designer, and the programmer must also design the protection technique to protect their system against infiltration.
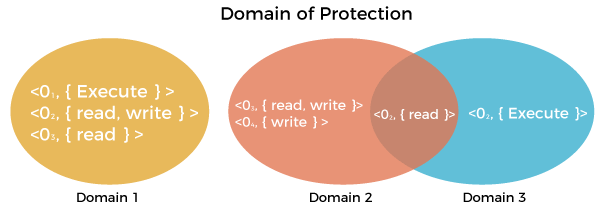
Domain of Protection
Various domains of protection in operating system are as follows:
- The protection policies restrict each process’s access to its resource handling. A process is obligated to use only the resources necessary to fulfil its task within the time constraints and in the mode in which it is required. It is a process’s protected domain.
- Processes and objects are abstract data types in a computer system, and these objects have operations that are unique to them. A domain component is defined as <object, {set of operations on object}>.
- Each domain comprises a collection of objects and the operations that may be implemented on them. A domain could be made up of only one process, procedure, or user. If a domain is linked with a procedure, changing the domain would mean changing the procedure ID. Objects may share one or more common operations.
Association between Process and Domain
When processes have the necessary access rights, they can switch from one domain to another. It could be of two types, as shown below.
1. Fixed or Static
In a fixed association, all access rights could be given to processes at the start. However, the results in a large number of access rights for domain switching. As a result, a technique of changing the domain’s contents is found dynamically.
2. Changing or dynamic
A process may switch dynamically and creating a new domain in the process.
Security measures of Operating System
There are various security measures of the operating system that the users may take. Some of them are as follows:
- The network used for file transfers must be secure at all times. During the transfer, no alien software should be able to harvest information from the network. It is referred to as network sniffing, and it could be avoided by implementing encrypted data transfer routes. Moreover, the OS should be capable of resisting forceful or even accidental violations.
- Passwords are a good authentication method, but they are the most common and vulnerable. It is very easy to crack passwords.
- Security measures at various levels are put in place to prevent malpractices, like no one being allowed on the premises or access to the systems.
- The best authentication techniques include a username-password combination, eye retina scan, fingerprint, or even user cards to access the system.
System Authentication
One-time passwords, encrypted passwords, and cryptography are used to create a strong password and a formidable authentication source.
1. One-time Password
It is a way that is unique at every login by the user. It is a combination of two passwords that allow the user access. The system creates a random number, and the user supplies a matching one. An algorithm generates a random number for the system and the user, and the output is matched using a common function.
2. Encrypted Passwords
It is also a very effective technique of authenticating access. Encrypted data is passed via the network, which transfers and checks passwords, allowing data to pass without interruption or interception.
3. Cryptography
It’s another way to ensure that unauthorized users can’t access data transferred over a network. It aids in the data secure transmission. It introduces the concept of a key to protecting the data. The key is crucial in this situation. When a user sends data, he encodes it using a computer that has the key, and the receiver must decode the data with the same key. As a result, even if the data is stolen in the middle of the process, there’s a good possibility the unauthorized user won’t be able to access it.