Server-side attack basics
In this section, we are going to do server-side attacks. To do this, first we are going to use information gathering, which is used to show us the installed programs, the operating system of the target, the running services on the target, and the port associated with these services. From these installed services, we can try and get into the system. We can do this by trying the default passwords.
There is a lot of people that install services and misconfigure them, so we will have another example of this as well. The first problem with these services is that sometimes, a lot of services are designed to give someone remote access to that computer, but they obviously need to have some security implementations. People often misconfigured these services, so we can take advantages of these misconfigurations and gain access to these computers. Another problem with these services is that some of them might even have backdoors. A lot of them will have vulnerabilities, like remote buffer overflow or code execution vulnerabilities, and this will allow us to gain full access to the computer system.
The simplest way of doing this is something that we have seen before, Zenmap. We use Zenmap with the IP of the websites. Using Zenmap, we will get a list of all these services, and then Google each one of them to see if they contain any vulnerabilities. We’ve seen before that the Metasploitable device is actually a website. If we want to get the IP of a website, we have to do is ping. For example, if we want to get the IP of Facebook, we have to ping facebook.com, and we will get their IP. Now we will be able to run Zenmap against Facebook IP and get a list of all the running services on Facebook. But, in this section, we are going to run Zenmap against Metasploitable device, which basically is a computer device.
We are going to run Zenmap in the same way we did before. To open Zenmap, We will open the terminal and type zenmap, and we’ll bring up the application. We can put any IP which we want to test. But, in this section, we are going to enter the IP of our target, of the Metasploitable device, which is 10.0.2.4 in our example. We are going to Scan, and this will give us a list of all the installed applications as shown in the following screenshot:
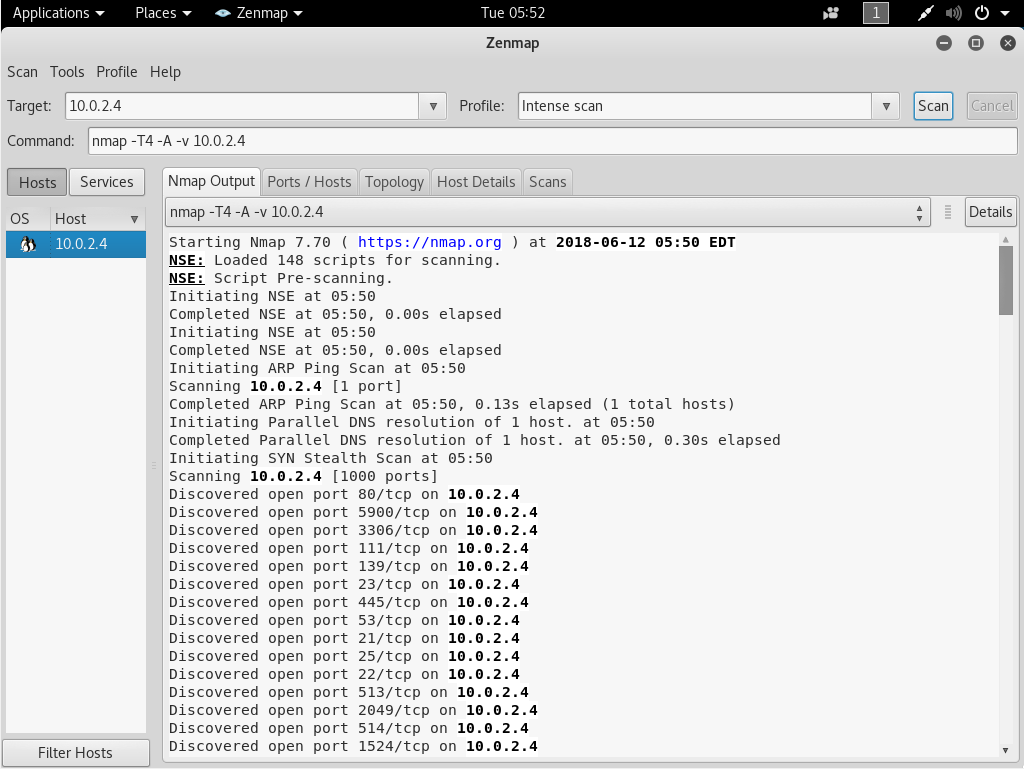
Once the scan is finished, we will have open ports and a lot of services. Now we will go on the Nmap Output tab, check port by port, read what the services are, and Google the name of the services.
For example, in the following screenshot, we have port 21 which is an FTP port. FTP is a type of service that is installed to allow people to upload and download files from a remote server. FTP service usually uses a username and a password, but we can see that this service has been misconfigured and it allows an anonymous FTP login. So in this, we will be able to log in without a password, note the next screenshot:
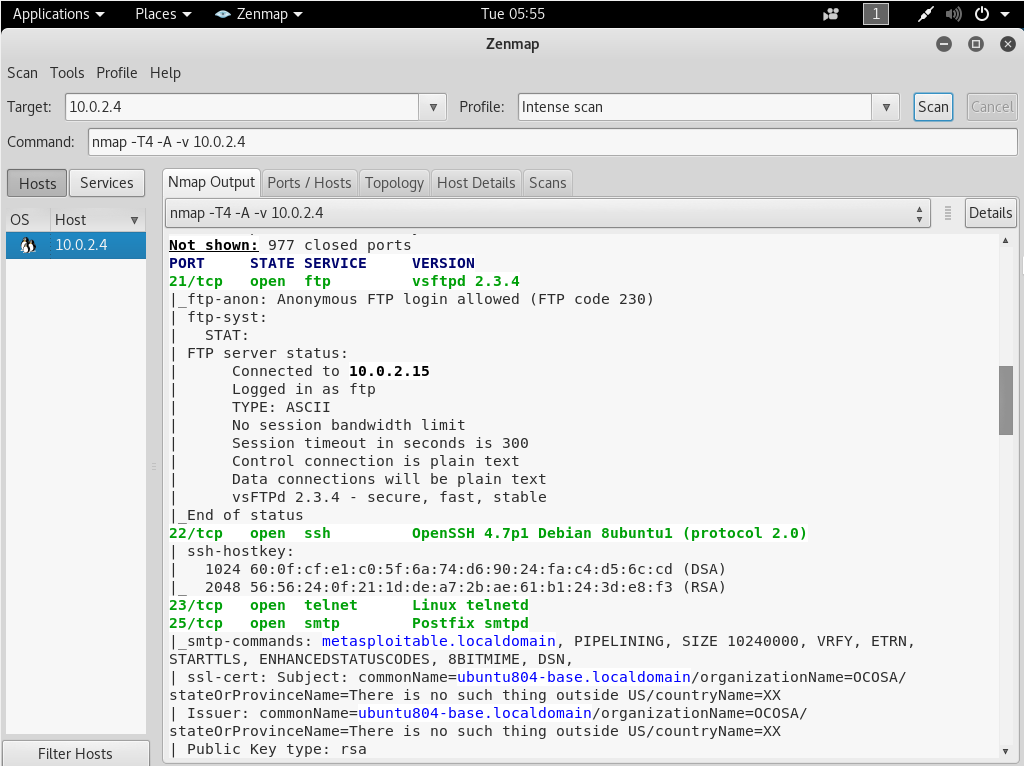
All we have to do is download an FTP client, such as FileZilla. Now, we will be able to connect using this IP address on port 21. We can also Google an FTP server, which in our case is vsftpd 2.3.4, and see whether it has any issues or if it has any misconfigurations, or if it has any known code execution exploits. Once we Google this, we can see that vsftpd 2.3.4 has a backdoor installed with it. It literally came with a backdoor when it was released. We need to Google the service one by one and check whether they have any misconfigurations or any exploits installed.
Now we will look at the port 512. Let’s assume we went on them one by one, we could not find anything, and we reached at the 512 TCP port, as shown in the following screenshot:
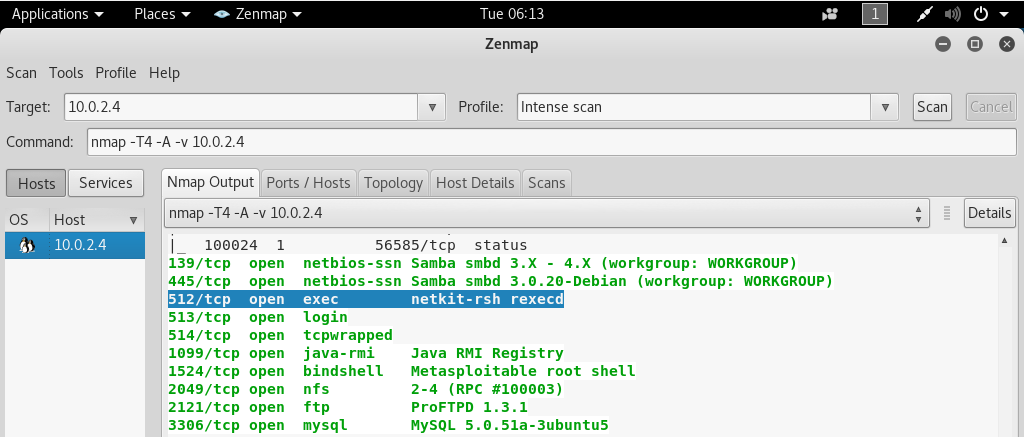
Now we are going to Google the service that is running on 512 port because we don’t know what it is. After Googling, we know that netkit-rsh is a remote execution program. If we manage to log in with this, we will be able to execute commands on the target computer. This program uses the rsh rlogin, which is a program that ships with Linux. Similar to SSH, it allows us to execute remote commands on the target computer.
Let’s go back and see how we can connect to the rsh rlogin service. Let’s look at the netkit-rsh package, and we can see that it is Ubuntu. The target computer is running on Ubuntu, and we can see that in here it uses the rsh-client service to connect. So, we need to install a rsh-client package to connect to that service. It is a client program for a remote shell connection. Now, use the following command to install rsh-client:

apt-get is going to install it and configure it for us. Once it is installed, we are going to use rlogin to log in, because the first page told us that it uses the rlogin program to facilitate the login process. We are going to do rlogin again, and if we don’t know how to use this app, we can use –help command to see how to use it, as shown in the following screenshot:
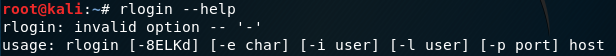
Here, important things are the username(-l) and host which is the target IP. Now we are going to do rlogin. We are going to put the username as root, which is the user with the most privileges on the system, and we will put 10.0.2.4, which is the target IP. Here is the command:

Now, we are logged into the Metasploitable machine. If we execute the id command to get the ID, we can see that we are root. If we execute the uname -a command, it will list the hostname and kernel that’s running on the machine. We can see that we are in Metasploitable machine with root access, shown as follows:
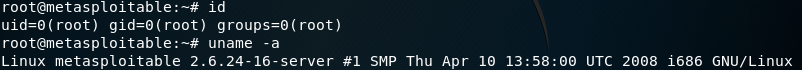
This is a basic manual way of gaining access to the target computer by exploiting the misconfiguration of an installed service. The rlogin service was not configured properly. All we had to do was just Google what came with that port, and we managed to log in and gain access to the target computer.
