Splunk Field Searching
In this section, we are going to learn How to do field searching in the Splunk. Also, we are going to learn about extracted field, index time, search time, using the field for searching.
Fields occur in several ways in the system data. Sometimes an area is a value that has a fixed, delimited location on a line, or a pair of names and values, where each field name has a single meaning. A field can be multivalued; that is to say, a field can have multiple values in a field in a single case.
Some examples of fields are clientips for IP addresses that access your Web site, time for event timestamp, and host for the site domain name.
Email address fields are one of the commonest examples of multivalue fields. Although the From field would only contain one email address, the To and Cc fields have one or more corresponding email addresses.
Fields are pairings of searchable names and values which distinguish one event from another. Not every case has the same fields and values. Use the fields to write more custom searches to get back the unique events you want.
Extracted fields
At index time and search time, the Splunk program extracts fields from the event data.
Index time
The time period from when the Splunk program obtains new data to when the data is written into an index. The data were analyzed in segments and incidents during index time. Extract default fields and timestamps, and add transforms are also done at this moment.
Search time
The time span is beginning when a search is started and ending when the search is ended. Several types of event processing occur during the search phase, such as search phase-field extraction, field aliasing, source type renaming, event type matching, etc.
For each event, the default fields and other indexed fields are extracted when indexing the data.
Search with fields
- If you are looking for fields, use the syntax
field name = field value syntax. - Field names are case sensitive, but field values are not.
- The wildcards can be included in field values.
- Quotation marks are needed where spaces are included in the field values.
Let’s do some digging.
- Click on Search to launch a new search in the App bar. Note that the default time span is set back to the Last 24 hours.
- To search for any values that begin with access in the sourcetype field, run the search below.
- Scroll through the search results to the list of events. If you’re familiar with Apache logs’ access combined format, you could recognize some of the details in each case, as IP addresses for the users accessing the website.
- The Fields tab is to the left of the Events column. As events that suit your quest are being retrieved, the sidebar Fields updates the lists of Selected Fields and Interesting Fields. These are the fields derived from the data by the Splunk app.
When we search, the Selected Fields list contains the default fields host, source, and sourcetype. These default fields appear in every event.
Interesting fields- They are fields in which at least 20 percent of events occur.
Specify additional selected fields
You can designate other fields to appear in the Selected Fields list. When you add a field to the Selected Fields list, the field name and field value are included in the search results.
Demo
Now let’s get our hand dirty on the Splunk platform by performing some of the field operations.
When data is uploaded in the Splunk platform, then it is automatically monitored by Splunk, and then it gets divided into a different field. Every field has some logical facts from the dataset.
For example, the field may contain information about the timestamp of the event, server name, http responses, login attempt, etc. For unstructured data type, the Splunk platform differentiates the fields into the numeric or string values depending on the data type.
Splunk assigns alpha (α) to the fields containing string value and hash (#) to the area, including the numerical value.
As we are going to continue with data that we uploaded earlier i.e., titanic dataset. By searching on the field as we did more first, we can notice that as we uploaded the data, Splunk automatically divided it into the different fields. For reference, you can see the image below.
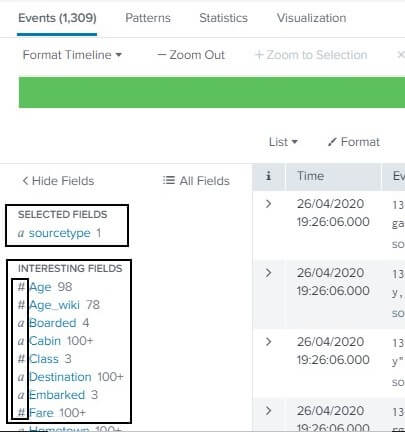
Opting the Field
We can select the fields that we want to display in our dataset. We need to click on the All fields present at the top right section of the FIELDS section. We can see that option in the above image. Click on that; then, a window will appear displaying you all the fields that you want to see in your uploaded data. You can tick the fields that you wish to display and untick the ones you don’t want to display. For the reference, you can take a look at the image below.
Besides the field, we can see that it also displays the value of the respective field, which means how many types of values the field contains, type – which tells the data type of the field and the percentage of the event the respective field is present.
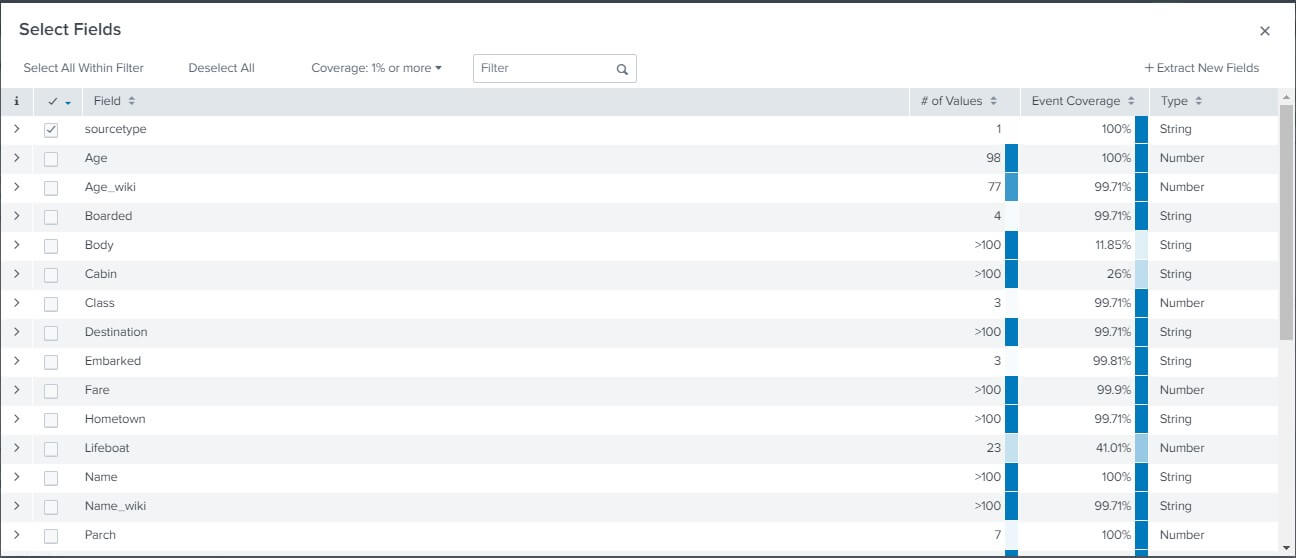
Summary of the Field
The detailed stats of the respective field are displayed just by clicking on the respective field.
It shows us all the values that the field contains, the count of each value, and also the percentage of the value in the dataset. When we click on the Age field, it shows us all the value it contains, as we can see it in the image below.
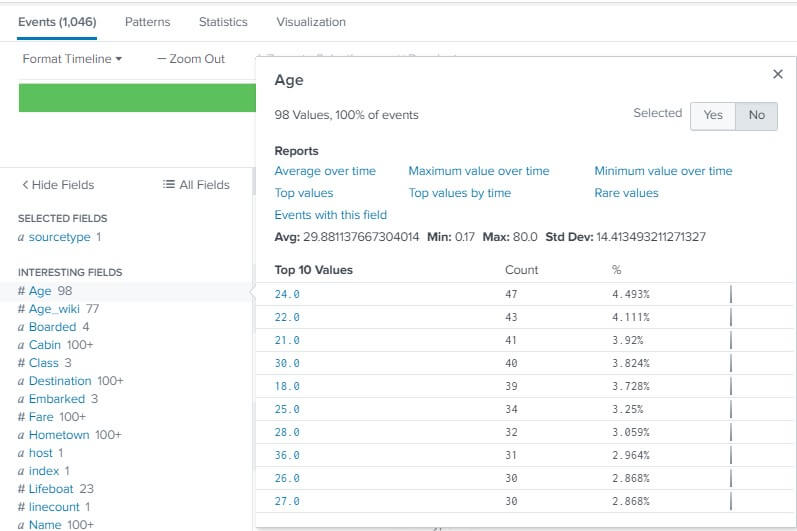
Use of field for searching
We can also insert the field name in the search box for searching for any specific field. We can add it either by writing the field name in the search box or also by just clicking on the field and adding it to the search box.
We can also use the wild card in a field, or we can search for a specific value.
In the example below, we have used the wild card in the Age field to search for all the values of the age in our data set. For reference, take a look at the image below.
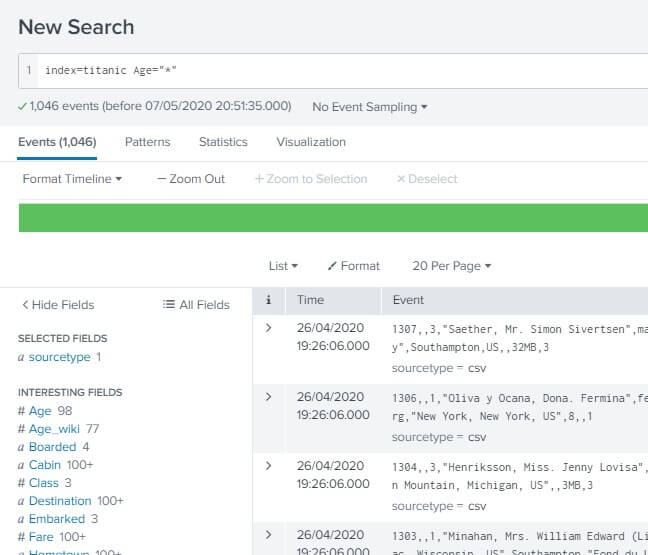
Now we have a basic understanding of the searching and also the knowledge of the field searching.
Hit the ground and explore more.
