MSFC scan
Now, we will log in using the username and password that we set when we installed the tool. In the above screenshot shows a web interface of Metasploit community:

Now, after log in, we can access the account and go to our user setting or log out. We can also check for software updates.
When we log in the first time, it will ask us to enter the activation key. The activation key will be sent to our email address which we put when we downloaded the tool. We should make sure that we enter a valid email address when we download the tool.
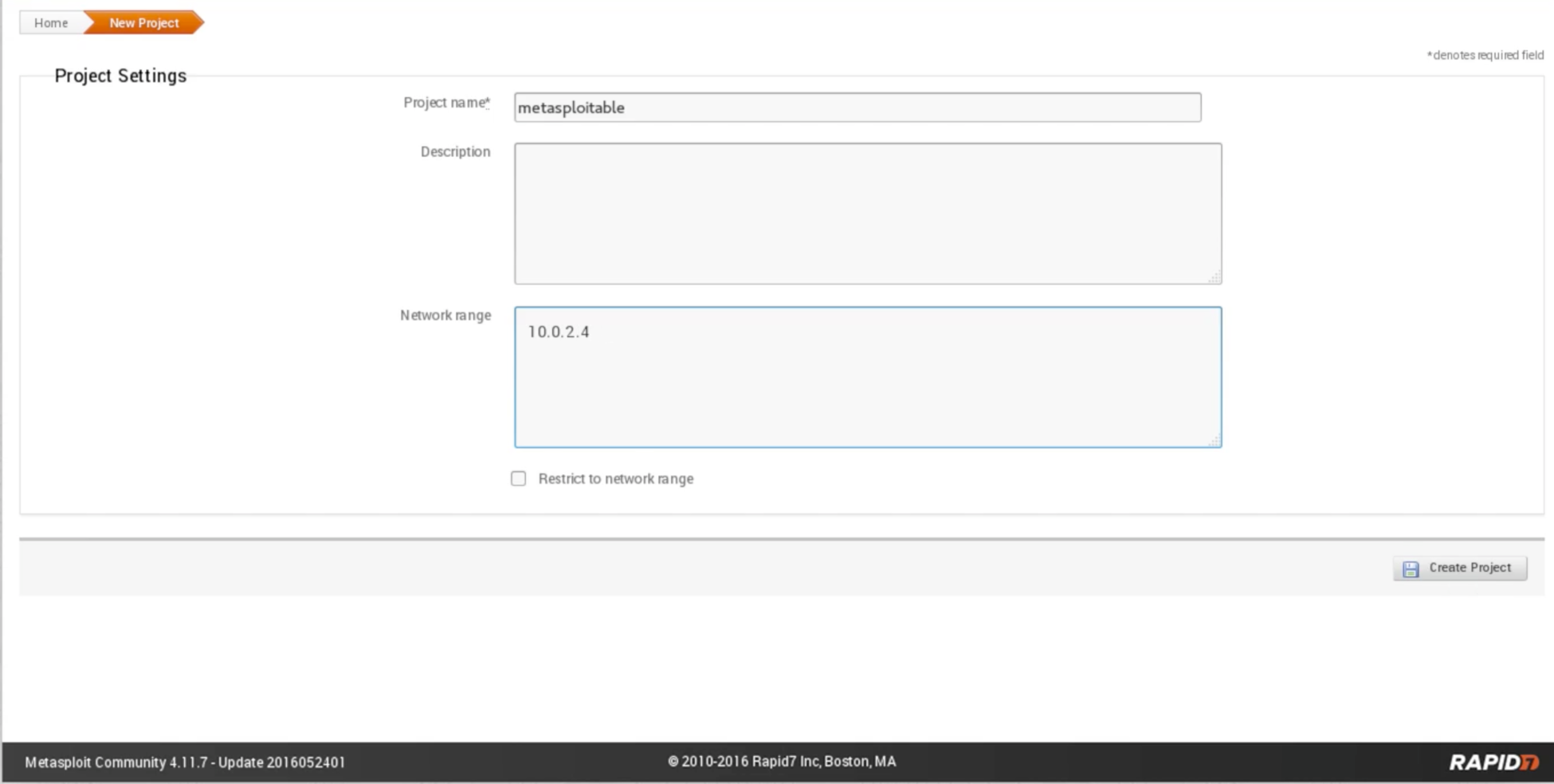
We are going to start a scan, and we are going to click on Project | New Project. We are going to call this project metasploitable, we are going to leave the Description empty, and then it is asking us for a Network range. We can set that the same way we did with Zenmap, and we can set it to a range. It actually has a range that is within our subnet at the moment, which is 10.0.2.1 up to 254. We can scan the whole network for vulnerabilities and exploits, but for now, we are going to target 10.0.2.4, which is the Metasploitable machine.
Now we will click on Create Project. The following screenshot shows all the discussed parameters:
Now, the project is created, and we are going to start a scan on it. We are going to go on the scan button on the left side of the screen and click that. To launch the scan, we have to go to the Show Advanced Options to set some advanced option. If we have a range, we can use the exclude-address to exclude some IPs. For example, if we were targeting the whole network from 1 to 254, we can exclude our computer from the search by just typing our IP which is 10.0.2.15. We can also put a custom Nmap argument because Metasploit will actually use Nmap to get the service and the installed applications. We can add additional TCP Ports or take away TCP ports. Again we can do the same. We can even set the speed. We also have the UDP service discovery. It actually discovers the service that is installed on the port. We can also set credentials. If the target computer uses some sort of authentication, we can set it up, but we are fine because our target does not use any of that. We can also set a tag for the target computer.
Now, we are not going to mess with these settings. We are going to keep everything the same to make it simple, and we are going to launch the scan. Once this scan is over, we will see how we can analyze and discover, and see what we can do with the discovered information.
