What is Metasploit?
It is an open-source project which offers the public resources to develop codes and research security vulnerabilities. It permits the network administrators for breaking their network to recognize security threats and also document which vulnerability requires to be defined first.
It is a type of project that facilitates Pen (Penetration) testing software. Also, it offers tools to automate the comparison of a vulnerability of a program and its patched (repaired) version. It also offers advanced evasion and anti-forensic tools. A few of these tools are created into the framework of Metasploit.
Let’s discuss some key points.
- The Metasploit Project facilitates a shellcode database, Opcode Database (out of data currently), Metasploit Pro, and Metasploit Express.
- Shellcode is a kind of exploit code where bytecode is included for accomplishing a specific goal. Common shellcode goals include performing the reverse telnet or adding the rootkit back to the machine of the attacker.
- Metasploit also provides the payload database that is allowing a pen tester to experiment with exploit goals and codes.
The Metasploit Project was inherited in 2009 by the computer security organization Rapid7. Metasploit Pro and Metasploit Express are the Metasploit Framework’s open core version with additional features. Open core is a way to deliver products that associate proprietary and open-source software. Rapid7 continues to developing Metasploit in association with an open-source community.
Metasploit Framework
One of the most effective creations of the Metasploit Project is the Metasploit Framework. Metasploit Framework is a software environment to develop, test, and execute exploits. It could be used for creating tools for security testing, exploiting modules, and as a pen-testing system. Originally, it was developed in 2003 as a movable network tool by HD Moore.
This framework is a very strong tool. It can be applied by ethical hackers and cybercriminals for probing systematic susceptibilities on servers and networks. Because it is an open-source framework, it can be easily used and customized with various operating systems.
The pen testing group can apply custom code or ready-made and address it in a network for probing for weak spots with Metasploit. Once the flaws are documented and identified as another threat hunting flavor, the information could be used for prioritizing solutions and addressing systemic weaknesses.
Metasploit Brief History
In 2003, the Metasploit Project was attempted by HD Moore to use as any Perl-based movable network tool along with assistance from Matt Millar core developer. It was completely transformed into Ruby in 2007. The license was inherited in 2009 by Rapid7, in which it remains the same as a segment of the Boston-based organization’s repertoire of the IDS signature evolution and targeted evasion tools, anti-forensic, fuzzing, and remote exploit.
- Portions of other tools are located in the Metasploit Framework. It is created in the Kali Linux OS.
- Rapid7 has improved two of the main open-core tools, Metasploit Express and Metasploit Pro.
- This framework is a go-to-exploit mitigation and development tool. Several pen testers have to implement each probe manually if prior Metasploit. It can be done by using a range of tools that might or might not have supported for writing their code by hand, addressing it on networks manually, and the environment they’re testing.
Who can use Metasploit?
Because of its wide range of open-source availability and applications, Metasploit can be used by almost everyone from the growing area of DevSecOps pros to many hackers. It is useful to those who require a reliable and easy-to-install tool. It can complete the task irrelevant of which language or platform is used.
This software is widely available and famous with various hackers. It reinforces the requirements for many security professionals for becoming familiar with this framework even when they do not use it.
Now, Metasploit contains 1677+ exploits arranged on 25 platforms, such as Cisco, Java, Python, PHP, Android, and others. Also, the framework carries approximately 500 payloads. A few of these payloads are below:
- Command Shell Payloads: Command shell payloads can enable the users to execute random or script commands against any host.
- Meterpreter Payloads: Meterpreter payloads permit users to commandeering device monitors with the help of VMC and for taking over sessions or download and upload files.
- Dynamic Payloads: These payloads permit users to produce specific payloads to avoid antivirus software.
- Static Payloads: Static payloads allow users to enable communication between several networks and port forwarding.
Modules of Metasploit
Metasploit offers us some modules for:
- Payloads: Sets of mischievous code
- Exploits: Tool utilized to take benefit of system weaknesses
- Auxiliary Functions: Supplementary commands and tools
- Listeners: Mischievous software that covers to obtain access
- Encoders: Used for converting information or code
- Shellcode: Code which is programmed for activating once in the target
- Nops: Instruction to protect the payload through crashing
- Post-exploitation code: Supports test deeper penetration when inside
Commands of Metasploit
Here are a few common commands of the Metasploit console we must know about. This Metasploit console is also referred to as the msfconsole which appears to be the batch file name that begins up the program.
Commands we must know about include:
- help: This command illustrates every available command within the msfconsole.
- show exploits: It illustrates various exploits we can execute. For example, windows/smb/ms17_010_etern exploit;
- show payloads: It illustrates the options of payloads we can run on an exploited system like uploading programs to execute, spawn the command shell. For example, shell_reverse_tcp exploit;
- use [exploit name]: This command instructs msfconsole for entering into a specific environment of exploit.
- info: It shows a specific exploit’s description we are using with its several requirements and options.
- show options: This command displays several parameters for a specific exploit we are working on.
- set PAYLOAD: This command permits us to set the particular payloads for our exploit. For example, set PAYLOAD
generic/shell_reverse_tcp; - show targets: It shows the target applications and OSes that could be exploited.
- set TARGET: This command permits us to choose a particular target application and OS when permitted by some exploits.
- set RHOST: It allows us to set the IP addresses of our target host. For example,
set RHOST
1.1.208; - set LHOST: It allows us to set the IP addresses of the local host for reverse communications required to open a reverse command shell. For example,
set LHOST
1.1.214; - back: This command allows us to exit from the current exploit platform we have loaded and then go back to the primary msfconsole prompt.
- exit: This command allows us to exit from the Metasploit console.
msfupdate is another essential command. Msfupdate is not just a command that we run inside the console, but the external program created inside the Metasploit Framework. This command can also be defined as a batch file positioned within the Metasploit Framework/bin folder which can download and then update the Metasploit running instance to the current version.
Architecture of Metasploit
The architecture of Metasploit consists of various important components. These components are required to completely use Metasploit power:
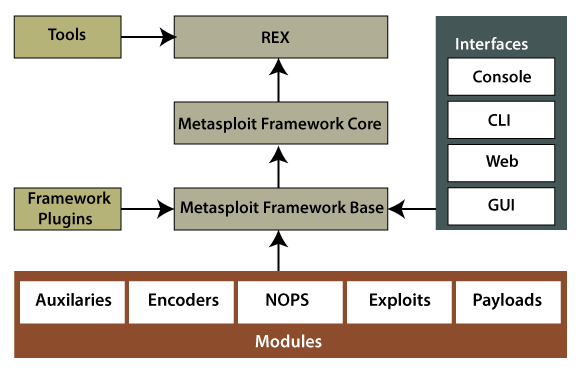
- Tools: These tools are the group of appropriate utilities.
- Plugins: At runtime, plugins are some loadable extensions.
- Interfaces: Interfaces provide users the capability for accessing Metasploit in so many different ways (web and CLI for instance).
- Libraries: These libraries are appropriate libraries of Ruby.
- Modules: Modules are used to implement specific tasks.
- REX: It handles almost every core function like setting up formatting, connections, sockets, and other functions.
- MSF CORE: It offers the common API and the original core that defines the framework.
Advantages of Metasploit
Let’s discuss some advantages of Metasploit.
1. Open-source
It is actively developed and open-source is the most important reason why we prefer Metasploit. Several other paid tools exist to carry out the penetration testing process. However, Metasploit permits users for adding their custom modules and accessing its code. The Metasploit Pro version is chargeable, although, for the sake of gaining, the community edition is preferred mostly.
2. Easy naming convention and support to test large networks
Metasploit is easy-to-use. However, here this feature defines the easy naming conventions of many commands. Metasploit facilitates ease while building a large penetration test of a network. For example, suppose we have to test any network having 200 systems. Rather than testing all the systems one-by-one, Metasploit can test the whole range automatically.
With parameters like Classless Inter-Domain Routine (short for CIDR) and subnet values, Metasploit can test every system to exploit the susceptibility. However, in any manual exploitation method, we may need to define the exploits onto 200 systems manually. Therefore, Metasploit is saving a large amount of energy and time.
3. GUI Environment
Metasploit provides third-party instances and friendly GUI like Armitage. These types of interfaces can ease the projects of penetration testing by facilitating services like functions on a button click, vulnerability management over the fly, and easy-to-shift workspaces.
4. Cleaner exits
Metasploit is liable to make a cleaner exit through a system. It is an important aspect if we know that this service will not immediately reboot. Also, it gives a lot of functions for post-exploitation like persistence which could support to maintain access to a server permanently.
